If you bank online then there is a good chance you will have been prompted to install a software product called Trusteer Rapport. It is recommended by NatWest, HSBC, First Direct and a whole list of others.
Trusteer Rapport helps increase the security of your Windows operating system by attempting to block keystroke logging attempts, screen capturing, validating the IP address of sites you visit (to protect against phishing/pharming), and more.
On the whole it looks like a good piece of software to have on your computer when combined with an up to date virus scanner, firewall, spyware blocker, and Windows automatic updates turned on. I use it on my computer and intend to continue to use it for now.
However there are a number of worries about the software. RLR UK Secure IT Services has written about some of the worries here and here.
I have a new worry to add to the list.
Password leakage
One of Trusteer Rapports security measures is to warn you if you enter a known password onto a new site. This is a security measure to protect against the password for one site being stolen by another sites phishing attempt.
This is all good stuff. However they have created a new potential problem in the way they have implemented the warning message. If you use the same password on multiple sites (as most people do), and someone discovers your password, then they can use Trusteer Rapport to get a list of other sites that you have asked Rapport which use the same password.
The malicious user will need access to your computer to do this, but if they have this access then all they need to do is enter the password on a new website and they will trigger this Trusteer Rapport warning dialog.
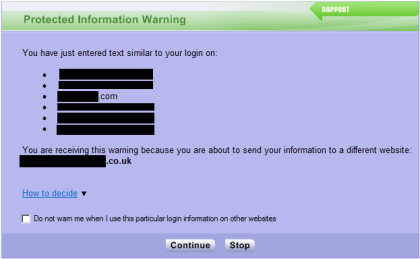
You will see that in this example dialog Trusteer Rapport has now leaked that this particular password is also the same password used on 6 other websites.
This means that instead of gaining access to one account, the malicious user could gain access to many of your password protected accounts.
Now you can argue that users should use a different password for each site, but in reality that is never going to happen. People have two choices (unless they have some kind of super brain), they either use a small number of passwords they can remember on all their sites, or they write the passwords down somewhere. Most people will reuse the passwords.
I think Trusteer would be better off changing this message so that it doesn’t print out the names of the websites. Perhaps Rapport could just print out a message saying that this password is in use on other websites, and that this is a new website that has not been given this password before.
Overall
Despite this I’d still recommend using Trusteer Rapport at the moment as it does many things which will increase the security on your computer. You must make sure you use it in combination with up to date anti-virus and anti-spyware.



Hello,
Thank you for reviewing our software and for recommending users to download and install Rapport.
Regarding your concern, as you rightfully mention, “The malicious user will need access to your computer to do this”. If someone manages to access your computer then there are much easier ways to log your login details for websites.
Guessing passwords against Rapport is by far the least attractive and most labor intensive method. Additionally, if your password is easy to guess then the criminals don’t need to access your computer to begin with, as they can guess it directly on the website itself.
At the end of the day, Rapport asks your permission to enable these mechanisms for each protected website and if you believe it is possible for malicious users to easily access your computer then you can choose not to enable this specific mechanism.
If anybody has any questions regarding this then please email support trusteer.com
Thanks
The Trusteer Team
It’s a testament to the company, that they have posted to comments sections on various web sites, which have voiced concern, to alleviate concerns.
I’m going to install.
At the end of the day as long as users exercise basic common sense i.e. safe internet browsing/software OS updates/Anti-Virus and the occasional Malware scan then chances are you will be safe. I would never trust software which keylogs or stores passwords – even if it does have strong encryption methods.
Forgive me if I am being dumb, but if this concerns you surely all you need to do is tick “do not warn me when I use this particular login information on other websites” at the bottom of the window?
Hi Paul – Yes you can do that. And that is something I do on my computers.
This sounds interesting.
However, until my bank gave me VERY STRONG advice during log in, to install Trusteer Rapport, I HAD NEVER HEARD OF THEM BEFORE.
Storing all my important passwords in one place on my PC is sure to provide all and sundry with an easy target.
Common sense has provided me with good security.
A good firewall, updated anti-virus etc AND if something behaves or looks odd, it probably is. Don’t click “yes” on dialogue prompts automatically and check for the “security lock” logo if in doubt.
Hi Andrew, I don’t believe that Trusteer Rapport does store any of your passwords. What it does is to store a hash of the password. There is no way to convert the password hash back into the password. All this allows Rapport to do is to see if you are entering the same password on multiple sites.
You can turn this behaviour off as Paul (in comment 4) states.
Or even better use a unique password for each site. (although this can be hard when you have over 100 logins passwords like I do!)
I still recommend using Trusteer Rapport along with a good virus scanner (e.g. Avast), spyware blocker (e.g. Spyware Blaster) and firewall. If you have Firefox you might want to consider installing Web of Trust, Long URL please, and HTTPS-everywhere. I have all of these installed!
Also changing your DNS to OpenDNS is worth considering, but if you do this make sure you open an account with them so that you have exclusive access to information about your IP address (something that can be an issue if you share your IP address with others).
Well, sorry but either way Trusteer seems to provide another target for baddies to exploit. How long before Trusteer updates are found to be to blame for passwords being stolen?
In order to easily maintain a unqiue password for every website, you can use a service like LastPass to store your passwords remotely. It can generate secure passwords for each new website you visit, you manage them by two-factor auth
One method for using different passwords yet be able to remember them all is to use some common password prepended to a unique part of the password.
i.e.
SomeSpecialP@$$word##bank1
SomeSpecialP@$$word##bank2
etc
This way your passwords remain tough but easy to remember.
With regard to whether it stores passwords or hashes, if it identifies *similar* passwords – as per the message in the dialogue box – surely it must be storing the password itself, not a hash?
” There is no way to convert the password hash back into the password.”
Two words: rainbow tables.
(http://en.wikipedia.org/wiki/Rainbow_table)
“In order to easily maintain a unqiue password for every website, you can use a service like LastPass to store your passwords remotely.”
“One method for using different passwords yet be able to remember them all is to use some common password prepended to a unique part of the password.”
A better approach is to use something like Stanford’s PwdHash (http://crypto.stanford.edu/PwdHash/) which doesn’t show the attacker any obvious pattern. It runs as client-side Javascript (which you can verify for yourself) in your browser, so you don’t have to trust any external service.